Designers
Design Map / Kana Knaak, Will Fletcher, Charles Hamilton, Morgan Keys, Jorge Arango | Cisco / Brian Maloney, Barbara Shain, Carolyn Morgan, Courtney Jennings, Domenique Johnson, Derrick Snider, Chloe Cooke-Warren, Jonathan Guerra, Carl Antone, Anat Borowitsh Lavy, Amoolya Kumar, Cardinal O’Neill, Alex Gonzalez Delgado, Alana Jackson, Wendy Hsu, Paulina Schuler, Annika Mammen
Year
2023
Category
Product
Country
United States
Three questions for the project team
What was the particular challenge of the project from a UX point of view?
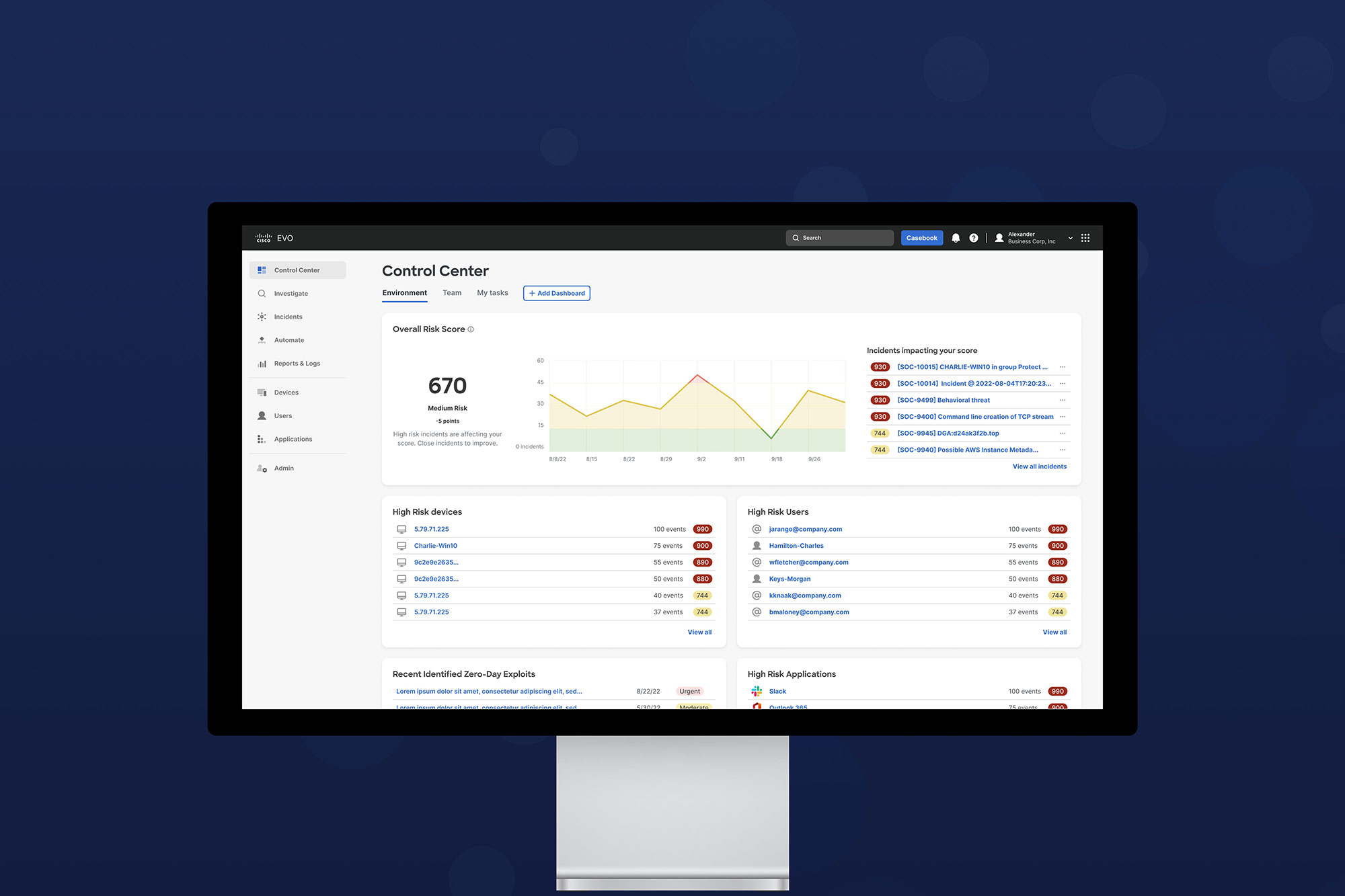
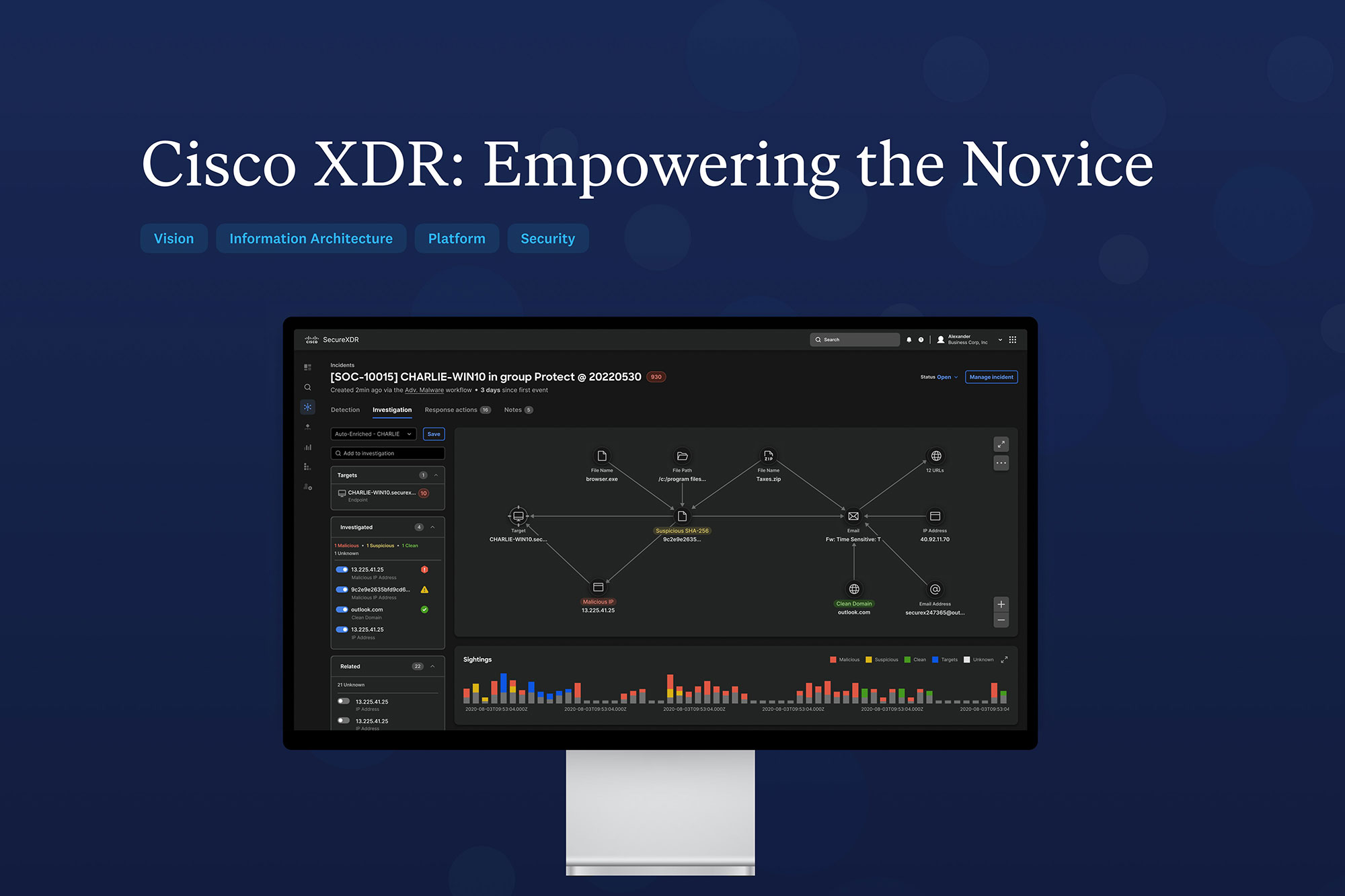
Since its beginnings, cybersecurity has been a game of cat and mouse between attackers and defenders. We now live in a world where unsophisticated attackers can arm themselves with fairly sophisticated tools that employ generative AI and machine learning to step up their attacks. Our challenge was creating a security tool that addresses modern techniques. Defenders need better automation, consolidated tools, impactful insights and correlative visuals to understand the situation and address it quickly and effectively. By understanding what defenders need, we were able to design our security tools to fit them and create a UX that enhances the analyst's ability to act quickly, which can make a huge difference in avoiding catastrophic breaches.
What was your personal highlight in the development process? Was there an aha!-moment, was there a low point?
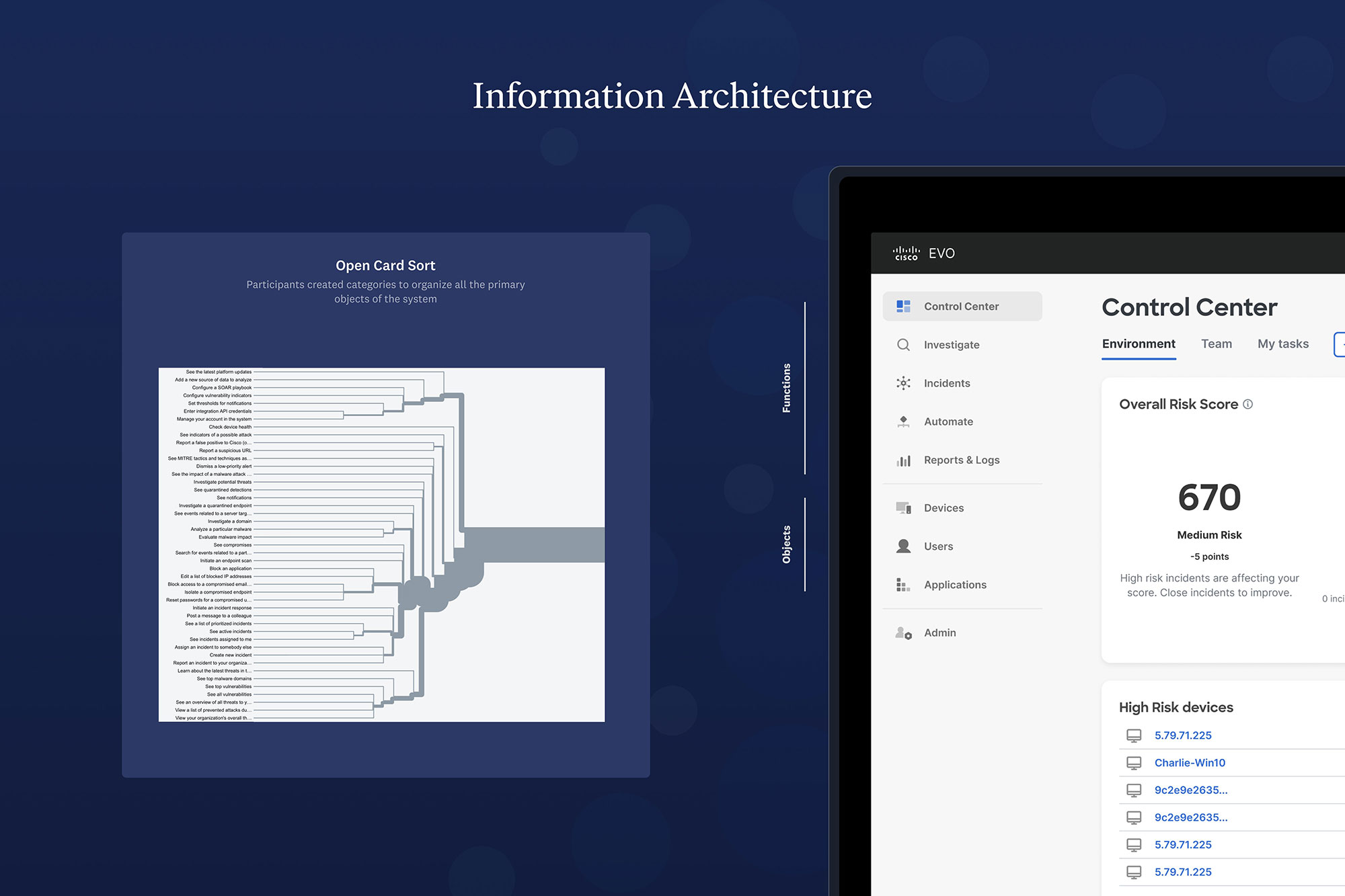
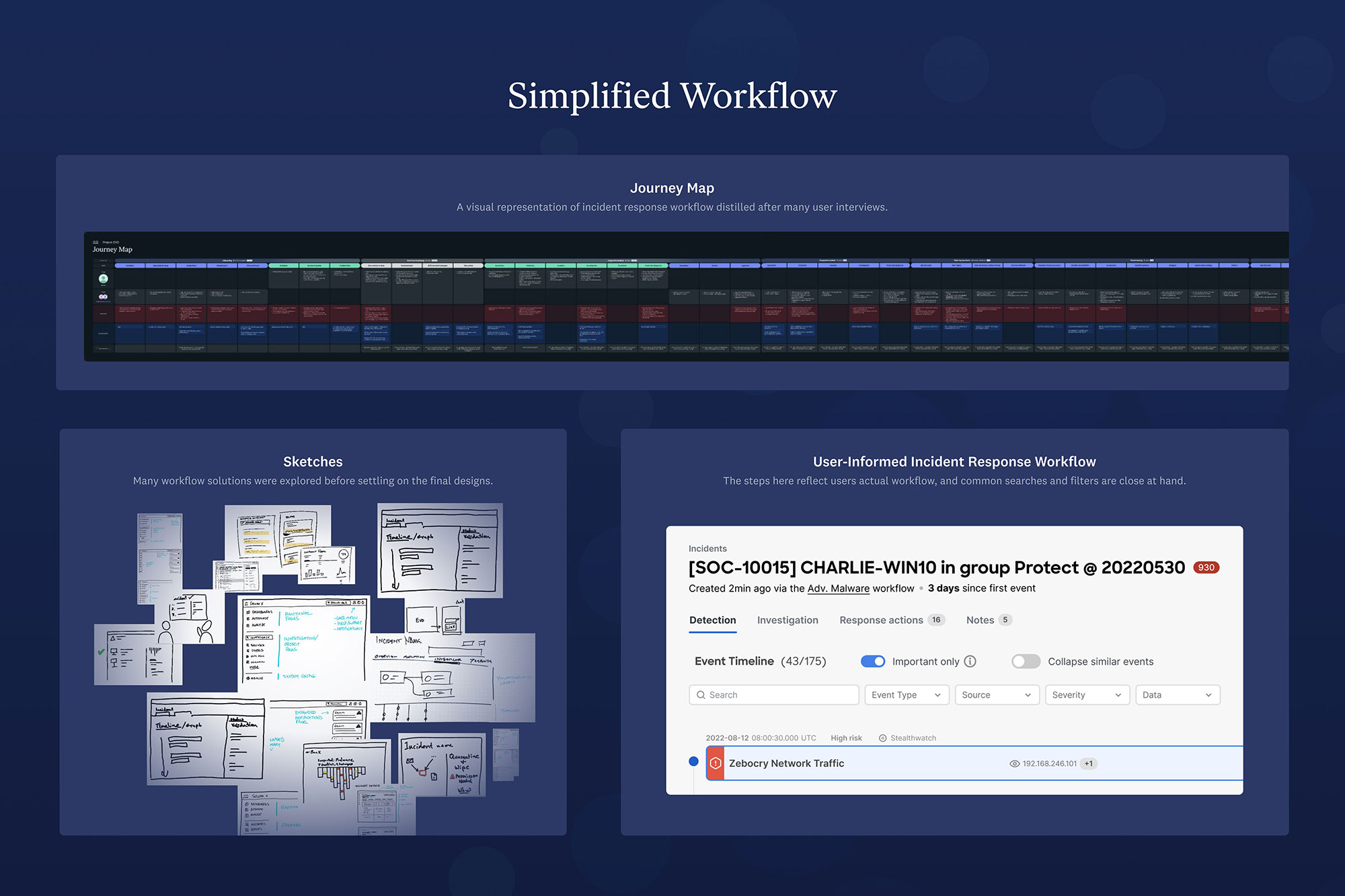
The aha moment came from analyst interviews. We discovered many people entering this role are Junior Analysts with limited security experience and a lot of uncertainty about how to handle threats. Our previous tools were mainly designed for senior people. Now, we have progressive disclosure, so a user can start with high-level insights and drill into contextual info to learn more about threats. We offer response actions that make suggestions based on threat types, and a worklog that enables better communication between junior and senior staff. The product has better contextual help and training baked in to support continuous learning. Addressing the Junior Analyst’s struggles became our product backbone. Customers are thrilled we adapted!
Where do you see yourself and the project in the next five years?
Because of the new prevalence of AI tools that can code and machine learning tools that can assist attackers from around the dark web, we predict that the next 5 years will be very busy as we continue to assist the security industry in their never-ending game of cat-and-mouse. There will always be creative and intelligent criminals looking for weaknesses and workarounds, and our team will always be ready with our own tools and solutions to keep the threats at bay.